UNDP has put together some advice given at an information security training session on what you need to do in order to protect yourself in the digital world.
How do you protect yourself online? Advice from a cyber security expert
August 29, 2022

Written by:
Anastasia Apetyk, cyber security expert from MINZMIN, an NGO
Iryna Kupchynska, Communications Specialist, UNDP Ukraine
Cyber security concerns everyone. We all transfer information, use social networks, and buy goods online. All these everyday actions require cyber security. After the beginning of the full-scale war on Ukraine, cyber security became even more important. “Everyone is fighting on the information front today,” said cyber security expert Anastasia Apetyk. That is why everyone needs to know the basic rules of how to protect yourself online.
At a UNDP-supported training session, experts explained what you need to do in order to enhance your online security. These simple rules will help you make sure that you and your information are protected.
Personal data
Fraudsters are after your personal data, so your first step is to secure that data.
Personal data comprises information that can identify a person. Such as a person’s full name, telephone number, email, residence address, plate number and car make, bank account number, bank card number and card validity, personal income, information about that person’s family members, photos, biometrical data, taxpayer identification code, signature, medical history, blood type, nationality, political or religious views, and sexual orientation. Personal data also include information about a person’s whereabouts, IP address and online identifier.
What do you need to do to protect all that data?
Be careful with technical devices. Although coffee spilled on your computer poses no threat to your personal data, it can temporarily disconnect you from your family. You should also be careful with your flash drives: you can easily transfer viruses or other malicious files together with your files. That is why it is better to email the documents you need or send them via the cloud.
Watch what information you post on social media. Photos of documents, dates of birth, exact addresses and telephone numbers, the time at which you go on holiday – all this can compromise your privacy. Do you know how you can quickly check whether or not you should post something on social networks? Think about whether or not you want to see that information on a billboard in a city. Changing your setting to “friends only” when posting something also does not guarantee you complete privacy: people can always take a screenshot and share your data.
Do not provide your personal data in response to seemingly official requests. These days, fraudsters often send emails or messages that mimic official ones and, for example, ask you to download a file or provide your personal data. They often seem to have been sent from an official email, but they either have errors in that email address, or do not contain the full name, title, or contact details of the person requesting information. If you are not sure whether or not you have received an official request, it is best to call the authority that has allegedly requested the information and get an official answer as to whether or not this information was actually requested. You should also bear in mind that no government agency will send you emails asking you to download a file, enter a code, or request that you provide your personal data.
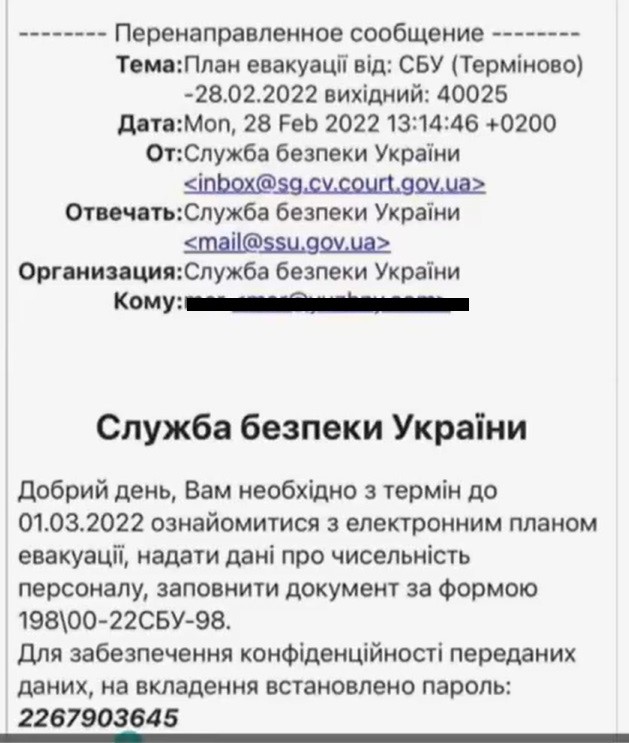
An example of phishing messages – a type of Internet fraud that is used to steal user data.
Password
Do not use the same password or very simple passwords. The 1111 password is the most commonly used password, which can be guessed instantaneously. It is also unsafe to use your year of birth as a password. You can check whether or not your password is secure on the How secure is my password? website (but do not type in your passwords on questionable websites!). Ideally, your password should contain at least 16 symbols, including uppercase and lowercase letters, digits and special characters.
Do not keep your social media, email, and work resource passwords written down on pieces of paper and stickers near your computer. Your desk drawers are also an obvious place where criminals look for passwords. It is better to memorize your passwords.
Use code phrases, such as “Purple Snow#48Candidate$ table + sobaka => (T@8l3 + S0bа4ka). This password contains random words, digits, characters and uppercase letters, and will be difficult to break. You can increase your cyber security by memorizing your passwords and by logging out of your email or other accounts at the end of your working day and logging in again in the morning.
Change your passwords from time to time. You should change your passwords at least every six months, but it is best to do it every three months. You should not enter your usernames and passwords in public places where CCTV cameras have been installed. If you have logged into your account on someone else’s device, change your password after that.
Two-factor authentication
Turn on two-factor authentication. It can be set it up on almost all messengers and social networks. This is an additional security feature that will help protect your computer or gadget. To access their account, the user has to provide more than one “proof of the authentication mechanism.” This includes:
- Special knowledge: information that is known only to one person. For example, a password or a pin code.
- A possession: a thing that belongs to one person or legal entity. For exaple, an electronic or magnetic card, token or a flash memory.
- A unique feature: For example, biometrics, unique natural features, such as a person’s face, fingerprints, or iris pattern.
Messengers
Messengers also have different security levels, with Viber considered the least protected.
The most protected popular messengers in Ukraine are WhatsApp, Signal and Telegram. However, it is better to email documents and other important files, or to transfer them by other secure means.
You should use different communication channels, such as alternative messengers, rather than relying on just one messenger. “Imagine what will happen if the messenger disappears one day? What will happen if the company blocks it? You will lose access to the contacts that were stored in that messenger. That’s why I also recommend to start using other messengers, such as Threema, Wickr Me, Wire, Element, and KeyBase,” says the expert.
SIM cards
SIM cards also need to be protected because mobile phone numbers are used to access social networks and mobile banking. You can do this in three steps:
- Link your SIM card to your ID;
- Set up a secret word (this feature is offered by mobile operators Kyivstar and Lifecell);
- Cancel the option of your SIM card’s remote recovery.
In this case, you will be able to get a replacement SIM card only if you have a document proving the identity of the number’s owner (a passport, driver's license, military ID, or a pension ID card). To prove that you are the number’s owner, you will have to provide your PUK code, or name two phone numbers that you have called or texted the most over the last 30 days.
Use different SIM cards for financial transactions (for example, to log into your Bank-ID and conduct transactions as a sole proprietor) and for communications and entertainment. You should not provide your financial telephone number and working email when registering loyalty cards in stores. Better yet is to set up a separate email address for registering on entertainment websites or obtaining discount cards.
Documenting and reporting online dangers
If your privacy has been compromised and your email, telephone number, or IDs have been put into the public domain, remember the rule of “Documenting and Reporting.” Document the leak of your data and report it to the cyber police.
If someone has posted your data on a social network without your consent, you should file a complaint against that user and the post that discloses your personal data. Every social network has its own mechanics of complaint. For example, on Facebook you need to click three dots next to the post, then “Report post,” “Something else” and “Privacy violation.”
These are simple but very important rules. Remembering what you need to do and remaining vigilant will make using online services much safer.
Let’s stay protected!
Background
The training session was led by Anastasia Apetyk, a lawyer, cyber security expert, co-founder of MINZMIN, an NGO, researcher of the digital rights and cyber security programme “Resilient Ukraine International Center for Defense and Security,” and the author of educational programmes. Apetyk has taught cyber security fundamentals to over 250,000 Ukrainians. In 2020, she was included in the Top 30 under 30 rating. In 2021, Apetyk was awarded a prize of the Cabinet of Ministers of Ukraine for special achievements in developing Ukraine.
In mid-May 2022, Apetyk conducted an open webinar on cyber security for librarians. This webinar was one of the online training sessions on cyber security held by Diia.Digital Education hubs in libraries. The webinar is available at the following link.
The training session was organized by the Ukrainian Library Association, together with the Digital, Inclusive, Accessible: Support to Digitalisation of Public Services in Ukraine Project (DIA Support Project), which is being implemented by UNDP in Ukraine with support from Sweden.
The Ukrainian Library Association has been a partner of the Ministry of Digital Transformation’s Diia.Digital Education project since January 2020. Libraries comprise the bulk of 6,200 digital education hubs – places anyone can visit to gain free access to the Diia.Digital Education website and do a course in digital literacy. The DIA Support Project also aims to make digital transformation in Ukraine more inclusive. Therefore, the project, in strategic partnership with the Ministry of Digital Transformation and the Ukrainian Library Association, contributes to the development of digital skills. The project, which was launched in 2021, aims to bridge the digital divide between generations and various social groups. Its main goal is to increase the accessibility of new digital solutions so that every man and woman in the country can use electronic services, and no one is left behind.

 Locations
Locations